Overview
Risk Cognizance: Cyber Solutions | Business Cybersecurity Software
In today's interconnected world, cybersecurity threats are constantly evolving, posing significant risks to businesses of all sizes. Risk Cognizance provides comprehensive cybersecurity software solutions designed to help organizations proactively manage and mitigate these threats, protecting valuable data and ensuring business continuity. Our platform empowers you to build a robust cybersecurity posture, comply with relevant regulations, and minimize the impact of cyberattacks.
Comprehensive Cybersecurity for a Dynamic Threat Landscape
Risk Cognizance's cybersecurity solutions goes beyond basic security measures, offering a holistic approach to managing cyber risks. We understand that cybersecurity is not just about technology; it's about people, processes, and governance. Our platform integrates these elements to provide a comprehensive defense against cyber threats.
Simplify Regulatory Compliance with Risk Cognizance
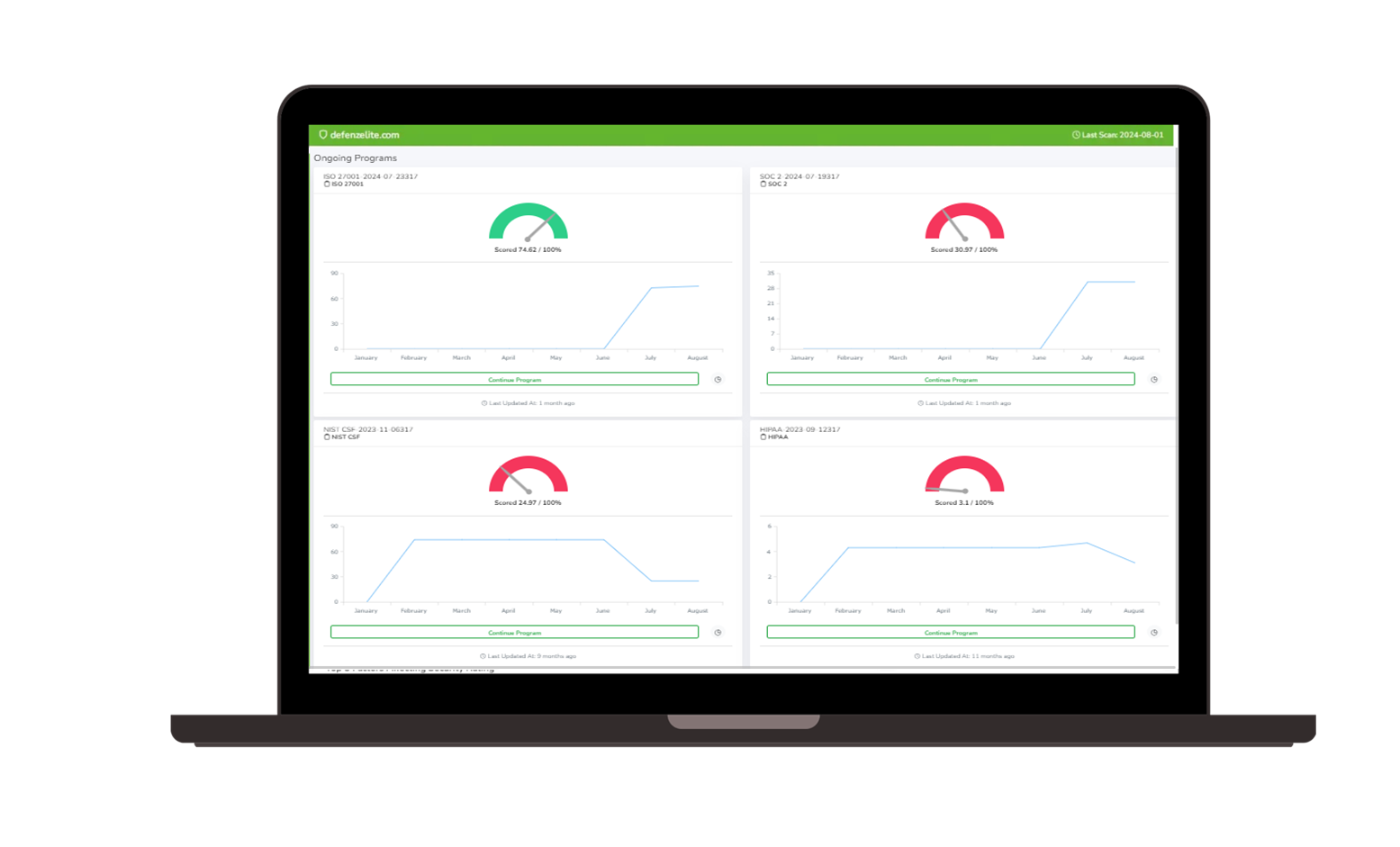
Choosing the right cybersecurity management tool is crucial for navigating today's complex regulatory landscape. Risk Cognizance simplifies compliance management with 24/7 audit monitoring, dynamic dashboards and reports, integrated risk assessments, and ready-to-go templates. Our solution helps you satisfy a wide range of cyber security compliance requirements, including SOX, HIPAA, PCI DSS, FISMA, GLBA, GDPR, ISO 27001, and more.

How Risk Cognizance Features Assist Businesses with Cybersecurity:
Risk Cognizance offers a suite of features that directly address critical cybersecurity challenges:
- Vulnerability Management:
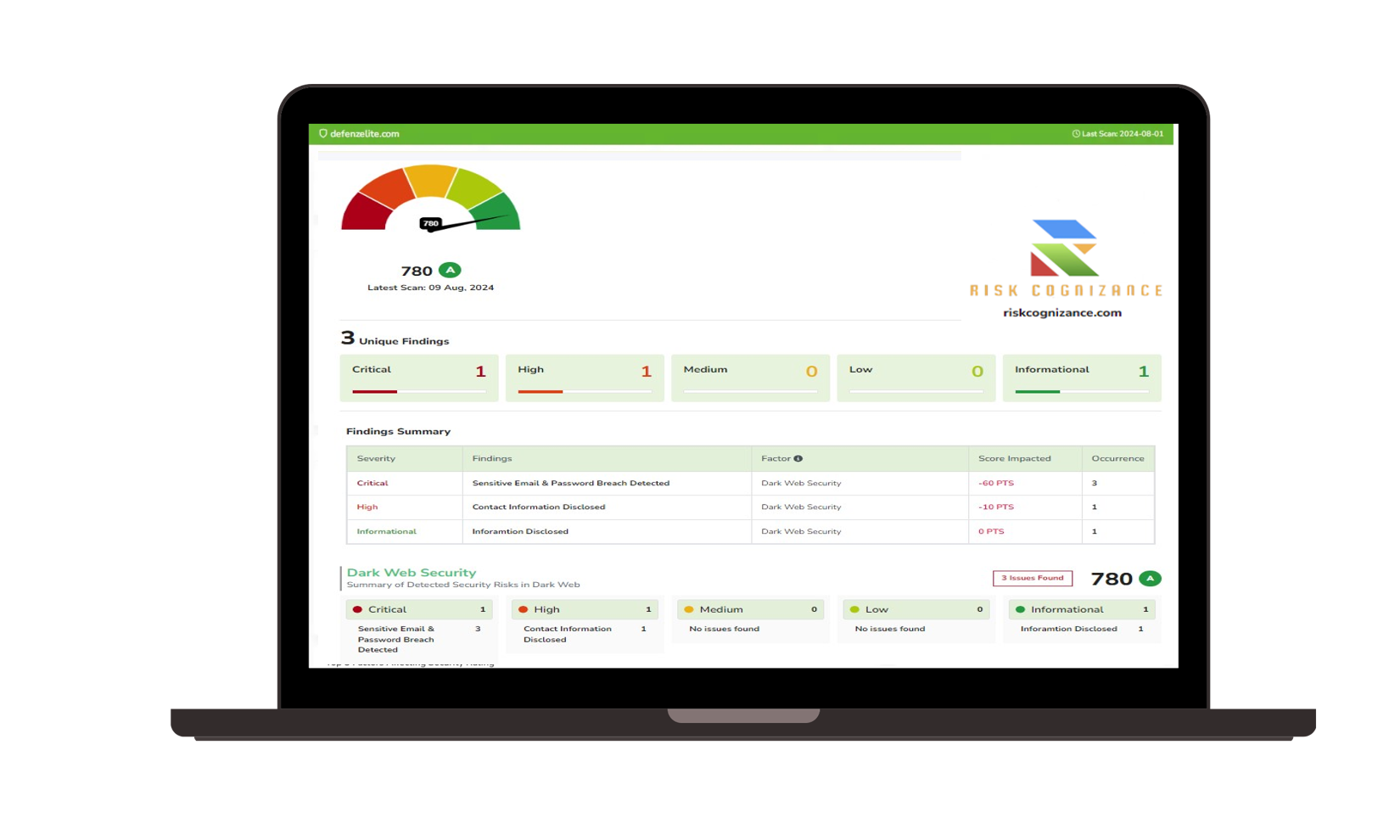
- Automated Vulnerability Scanning: Regularly scan your systems and applications for known vulnerabilities, identifying weaknesses before they can be exploited.
- Prioritized Remediation: Prioritize vulnerabilities based on their severity and potential impact, allowing you to focus on the most critical issues first.
- Vulnerability Tracking and Reporting: Track remediation efforts and generate reports to demonstrate progress and identify recurring vulnerabilities. This helps prevent repeat incidents and strengthens overall security.
- Incident Management:
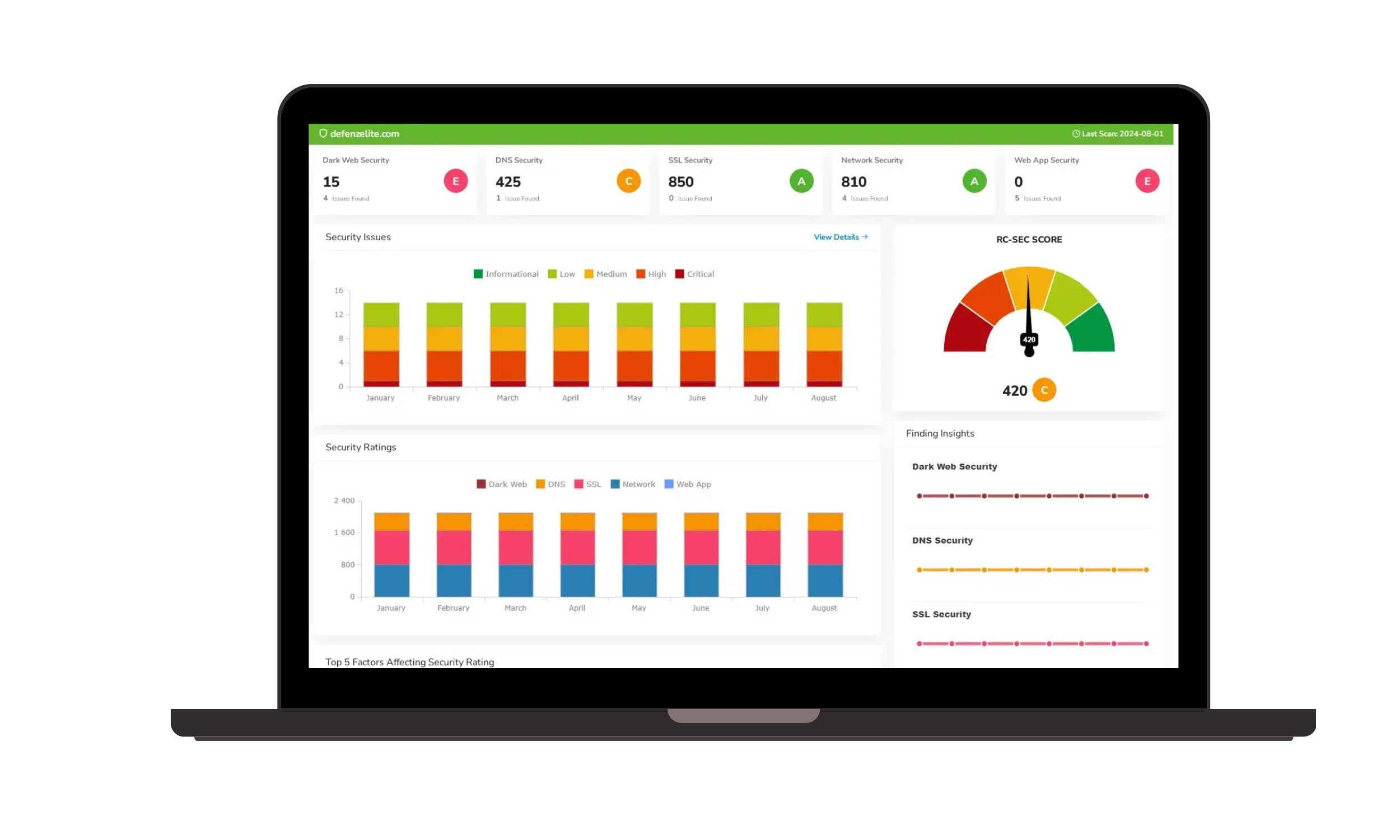
- Automated Incident Detection and Alerting: Detect suspicious activity and automatically generate alerts, enabling rapid response to potential incidents.
- Incident Response Workflows: Streamline incident response processes with predefined workflows, ensuring consistent and effective handling of incidents.
- Incident Tracking and Reporting: Track incident details, response actions, and lessons learned to improve future incident handling. This minimizes damage and downtime during and after an attack.
- Risk Assessment and Management (with a Cybersecurity Focus):
- Cyber Risk Identification: Identify specific cyber threats relevant to your organization, such as phishing, ransomware, malware, and data breaches.
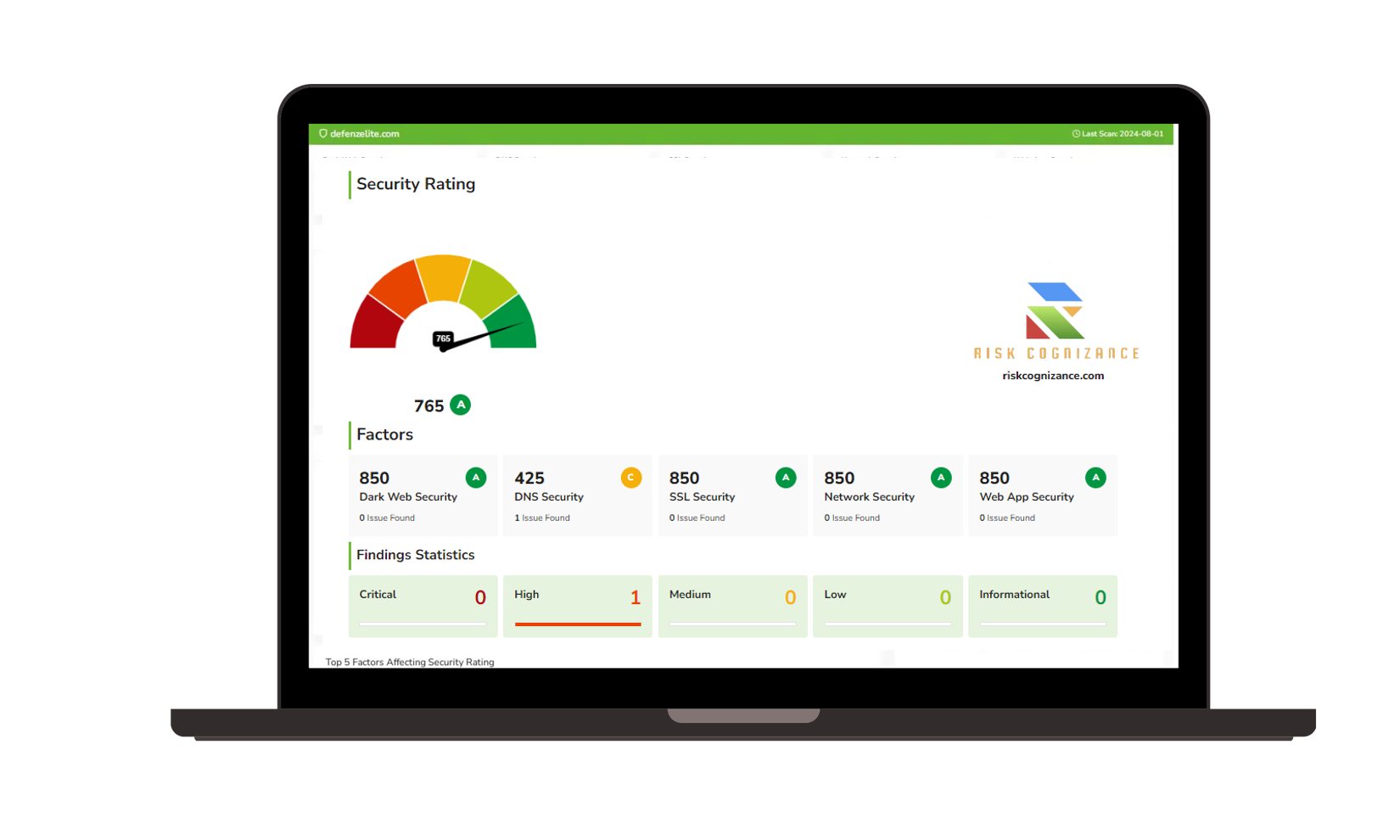
- Cyber Risk Assessment: Assess the likelihood and impact of these threats, considering factors such as vulnerability severity, attacker motivation, and potential business impact.
- Cyber Risk Mitigation: Develop and implement mitigation strategies to reduce cyber risks, such as implementing security controls, providing security awareness training, and developing incident response plans. This allows organizations to proactively prepare for and defend against cyberattacks.
- Compliance Management (for Cybersecurity Regulations):
- Framework Mapping: Map security controls to relevant cybersecurity regulations and frameworks, such as NIST Cybersecurity Framework, ISO 27001, and GDPR.
- Compliance Tracking and Reporting: Track compliance status and generate reports to demonstrate adherence to regulatory requirements. This ensures organizations meet legal and industry standards related to cybersecurity.
- Security Awareness Training Management:
- Track Training Completion: Monitor employee completion of security awareness training programs.
- Identify Training Gaps: Pinpoint areas where additional training is needed to address specific security risks. This helps create a human firewall, reducing the risk of human error leading to security breaches.
- Third-Party Risk Management (with a Cybersecurity Focus):
- Assess Third-Party Security Posture: Evaluate the cybersecurity practices of your vendors and suppliers to identify potential risks to your own organization.
- Monitor Third-Party Compliance: Track third-party compliance with security requirements and contractual obligations. This minimizes the risk of supply chain attacks and data breaches originating from third parties.
 |  |
 |  |
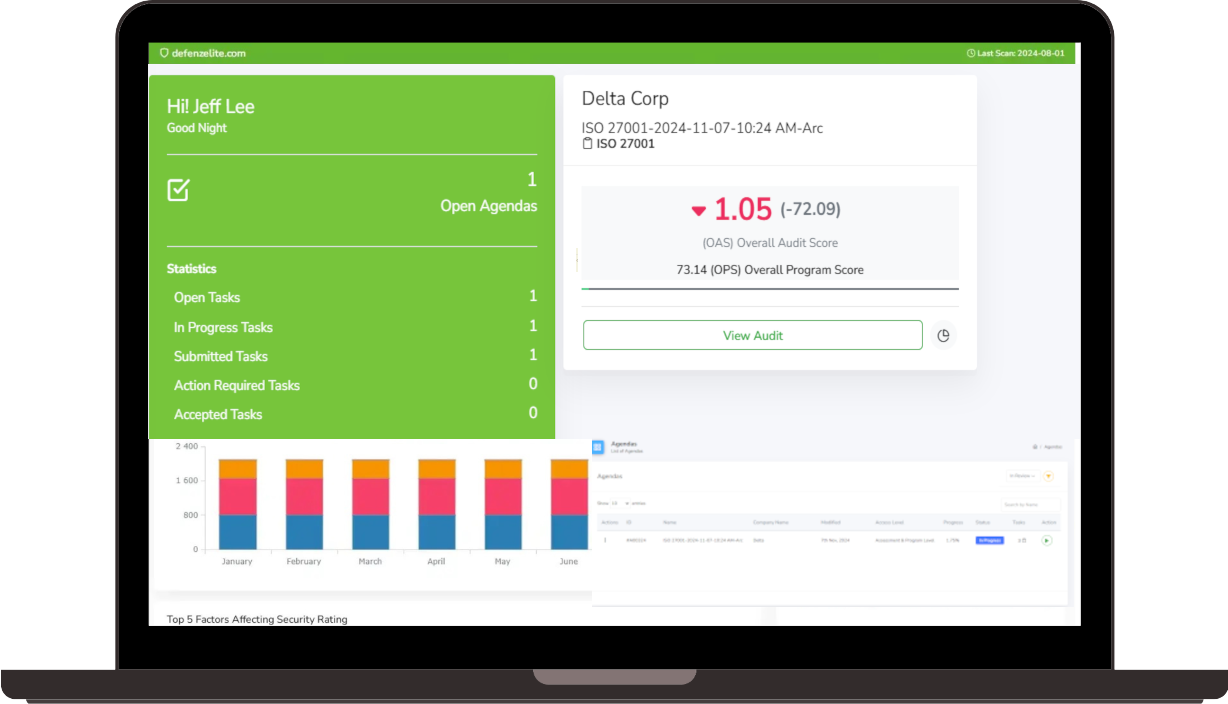 |  |
Benefits of Using Risk Cognizance for Cybersecurity:
- Reduced Risk of Cyberattacks: Proactive threat detection and mitigation significantly reduce the likelihood and impact of cyberattacks.
- Improved Security Posture: Strengthen your overall security posture through comprehensive risk management and compliance activities.
- Enhanced Compliance with Cybersecurity Regulations: Ensure adherence to relevant cybersecurity regulations and industry standards.
- Faster Incident Response: Streamlined incident response processes minimize downtime and damage in the event of a cyberattack.
- Improved Stakeholder Confidence: Demonstrate a strong commitment to cybersecurity, building trust with customers, partners, and regulators.
Who Can Benefit from Risk Cognizance Cyber Solutions?
Risk Cognizance is suitable for organizations of all sizes and across various industries, especially those handling sensitive data or operating in regulated industries.
Choose Risk Cognizance for Your Cybersecurity Needs
Risk Cognizance is the ideal cybersecurity software solution for organizations seeking to proactively manage cyber risks, protect their valuable data, and ensure business continuity. Contact us today to learn more and request a demo.
Request Callback
